I recently served as a reviewer for the kWAPTA (Certified Web App Penetration Testing Apprentice) exam. Reviewing candidate performance gave me a very clear picture of what works, what candidates commonly miss, and how this exam is actually meant to be approached.
kWAPTA is a foundation-level certification focused on validating real-world web application penetration testing skills in a controlled, beginner-friendly environment. Exam Link: kWAPTA
In this article, I’ll share exactly how I approached the exam - and what I observed as a reviewer - so you can maximize your chances of passing.
What the Exam Really Tests
The exam provides a single web application hosted on a dedicated domain which will be used for the entire exam. The candidate needs to analyze the application, understand its behavior, identify and exploit common security weaknesses & submit the flag.
From reviewing the exam, I can confidently say that this is not about advanced exploitation or complex tooling. The exam rewards methodical thinking, observation, and understanding of fundamentals. You can see the exam syllabus here:
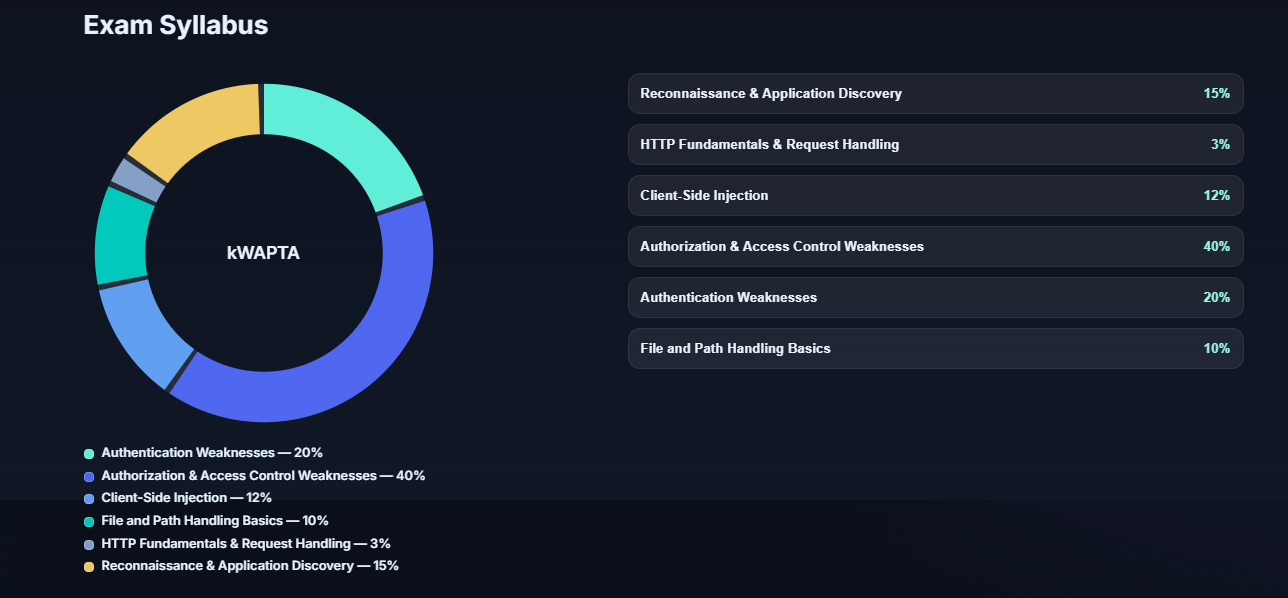
Most questions are hands-on and require you to identify a vulnerability and capture a flag as answer.
My Practical Approach (And What I Looked for as a Reviewer)
1. Reconnaissance Comes First — Always
Reconnaissance is the key. When you receive the target domain:
- Browse the application like a normal user.
- Click every feature and understand what the application actually does.
- Observe login flows, session behavior, input handling, and error messages.
- Pay attention to URLs, parameters, cookies, and redirects.
2. Follow the Question Flow
The exam questions are intentionally structured to guide your testing process. Instead of jumping randomly:
- Read each question carefully.
- Let the question guide where you should look and what to test.
- Treat the questions as a workflow rather than isolated tasks.
3. Test Common Vulnerabilities — Keep It Simple
The vulnerabilities align closely with the OWASP Top 10 and real-world beginner scenarios:
- Authentication: Weak login logic, insecure session handling.
- Authorization: Accessing restricted functionality or data.
- Client-side Injection: Basic XSS and input validation issues.
- File & Path Handling: Directory traversal or unsafe file handling.
- Error Handling: Verbose errors revealing useful information.
You won’t be given exact endpoints or told where a vulnerability exists. Instead, you need to test the application like a real pentester, discovering issues through observation and hands-on testing.
4. Tools:
Browser + Burp Suite Is Enough.
5. Capture Flags Carefully
Each practical question typically requires submitting a flag. Make sure you:
- Understand exactly what the question is asking.
- Verify the vulnerability clearly.
- Submit the correct output or value.
Who This Exam Is Best For
kWAPTA is ideal for:
- Students entering cybersecurity.
- Junior penetration testers.
- Developers and QA engineers learning security.
- SOC and blue team members transitioning to offensive security.
- Anyone wanting structured, hands-on web security experience.
Final Thoughts
From both personal experience and reviewing the exam, I can confidently say that kWAPTA rewards clarity, patience, and fundamentals. If you perform proper reconnaissance, follow the question flow, and test common vulnerabilities systematically, passing the exam is very achievable.
This certification is an excellent starting point for anyone serious about web application security. If you’re preparing for kWAPTA — keep it simple, stay curious, and trust the methodology.
Good luck ✌

